Network Monitoring Techniques
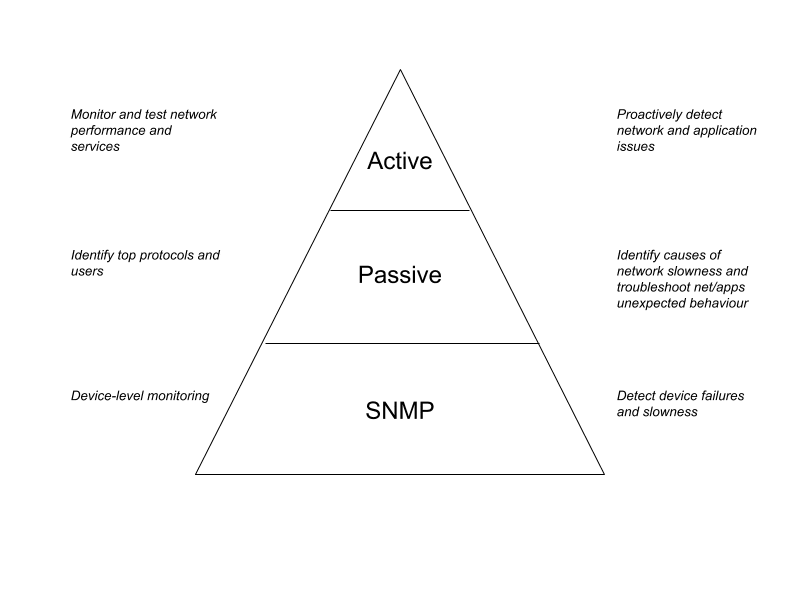
Whether or not you are new to network monitoring, there are three main network monitoring techniques you should know about. These three techniques are:
- SNMP-based monitoring
- Passive analysis and
- Active monitoring
When I explain the main difference between these three techniques, I simply say that SNMP is good at monitoring the status of network devices, passive analysis to view how the network is consumed by users and applications, and active monitoring to make sure that services are functioning and performing as expected.
Let’s review each one of them starting from SNMP, which stands for Simple Network Management Protocol. For each network monitoring technique, we’ll also provide some command line tools to familiarize with the concept.
SNMP Overview
SNMP is an Internet standard developed to monitor network devices. SNMP is used by network management stations to request information to a network device, also called network element. This standard can also be used to push configuration changes (snmpset) to network elements and to receive notifications (snmp traps) when problems occur. In this context, a network element could be, for example, a router, a switch, or a server.
The information requested to a network element via SNMP could be the CPU utilization, the amount of free disk space, or how many packets or bits were sent and received across its network interfaces. Each resource of a network element is represented by an Object Identifier (OID). Each device has a set of OIDs available. Some of these are standardized across manufacturers. Other OIDs are specific to a vendor and device.
SNMP queries are organized into sets of Management Information Base (MIB) files. Most network monitoring solutions in this category allow the import of custom SNMP MIB files to integrate with a specific device.
SNMP Commands Examples
If you are a Linux or Mac OS X user, then you have access to a set of SNMP command line utilities (Windows users may have to install them). I found two commands in particular, snmpget and snmpwalk, that are very useful. I’ll use these commands to demonstrate how SNMP works and what type of information this type of network monitoring technique offers.
The snmpget command allows you to query a network element specific SNMP OID at and retrieve associated information. In the following example, I am querying a local router by IP (192.168.1.1) to discover its hostname (OID = SNMPv2-MIB::sysName.0):
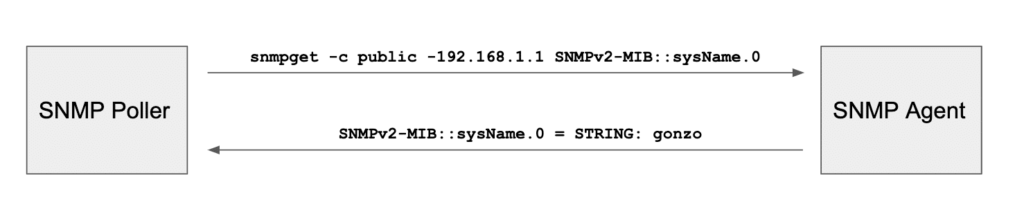
snmpget -c public 192.168.1.1 SNMPv2-MIB::sysName.0 SNMPv2-MIB::sysName.0 = STRING: 3725-lab-route
In this following snippet, I am running a snmpwalk command against the same router. The nice thing about snmpwalk is that it returns all OIDs available on that specific network element. In this case, I am truncating most of the output for sake of space …
snmpwalk -c public 192.168.1.1 SNMPv2-MIB::sysDescr.0 = STRING: Cisco IOS Software, 3700 Software (C3725-ADVIPSERVICESK9-M), Version 12.4(3j), RELEASE SOFTWARE (fc1) Technical Support: http://www.cisco.com/techsupport Copyright (c) 1986-2007 by Cisco Systems, Inc. Compiled Fri 14-Dec-07 01:14 by stshen SNMPv2-MIB::sysObjectID.0 = OID: SNMPv2-SMI::enterprises.9.1.414 DISMAN-EVENT-MIB::sysUpTimeInstance = Timeticks: (492591665) 57 days, 0:18:36.65 SNMPv2-MIB::sysContact.0 = STRING: SNMPv2-MIB::sysName.0 = STRING: 3725-lab-router SNMPv2-MIB::sysLocation.0 = STRING: SNMPv2-MIB::sysServices.0 = INTEGER: 78 SNMPv2-MIB::sysORLastChange.0 = Timeticks: (0) 0:00:00.00 ...
Passive Monitoring
Passive network monitoring is a technique that relies on “listening” to network traffic to determine its utilization. By doing so, a passive network monitoring tool can reveal what website and applications network users are accessing and identify top talkers as well as top applications. Top talkers refers to the network users that are consuming most of the bandwidth. This technique is widely used in security and surveillance, especially in SIEM (Security Information and Event Management) and DPI (Deep Packet Inspection) products.
There are three ways to passively monitor a network. The first one is by using an in-line device called network TAP. Network TAPs are dedicated devices installed in-line where user traffic flows. A network TAP replicates the entire content of the frames (layer 2) flowing across.
The second method relies on configuring a SPAN (Switch Port of ANalysis) port on a network switch. The switch will send all traffic flowing across a specific interface of VLAN to a destination port to which a traffic collector is connected.
The third method relies on configuring a flow analysis protocol on a networking hardware (either router or switch). There are proprietary flow protocols, such as NetFlow which was developed by Cisco, and standard ones, such as IPFIX which was developed by IETF.
What’s the best solution for passive monitoring? It depends really from the use case and information that you want to extract. In general, use a TAP or a SPAN if you need to capture the content, or payload, of network traffic. Use a flow-based protocol if you just need to inspect the header information to gather statistics on the traffic flowing across a network device or segment.
Passive Analysis Tools
The best way to learn more about the passive analysis monitoring technique is to install tcpdump, which is a data-network packet analyzer computer program that runs under a command line interface. If you prefer working with a GUI, you can use Wireshark.
Once installed on a computer, the user can capture network traffic sent and received on that same computer. In alternative you can connect that same computer to the output interface of a TAP or a SPAN port to analyze capture traffic.
In the following example, I am running tcpdump on my Wi-Fi interface, and logging all traffic sent and received to host google.com. On a separate console, I am running a ping test for demonstrating what I am able to capture with tcpdump.
tcpdump -i en0 host google.com tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on en0, link-type EN10MB (Ethernet), capture size 262144 bytes 18:46:33.471706 IP 172.29.0.147 > iad30s07-in-f14.1e100.net: ICMP echo request, id 29199, seq 0, length 64 18:46:33.490502 IP iad30s07-in-f14.1e100.net > 172.29.0.147: ICMP echo reply, id 29199, seq 0, length 64 18:46:34.474352 IP 172.29.0.147 > iad30s07-in-f14.1e100.net: ICMP echo request, id 29199, seq 1, length 64 18:46:34.487174 IP iad30s07-in-f14.1e100.net > 172.29.0.147: ICMP echo reply, id 29199, seq 1, length 64 18:46:35.479323 IP 172.29.0.147 > iad30s07-in-f14.1e100.net: ICMP echo request, id 29199, seq 2, length 64 18:46:35.491912 IP iad30s07-in-f14.1e100.net > 172.29.0.147: ICMP echo reply, id 29199, seq 2, length 64
I encourage you to learn more about how to use tcpdump. It’s a great tool that can help you troubleshoot the most head scratching network problems such as IP conflicts, don’t fragment issues, and more.
Active Network Monitoring
Active network monitoring is the ultimate technique used to proactively detect network and application issues. This technique works by performing continuous testing and verification of network services and applications. In the application monitoring world, this technique is also referred to as synthetic monitoring.
An active network monitoring system works by sending real traffic across a network. When testing an application or a service, the system performs a real transaction with the system. In either cases, active network monitoring periodically verifies that a network is able to deliver traffic.
Internet Service Providers monitor service level agreements by implementing different standards (RFC 2544) and protocols (TWAMP/OWAMP). Their goal is to assure that they honor Service Level Agreements (SLA) to their customers. In the enterprise world, this can be accomplished the same way with active network monitoring.
There are two main benefits of active monitoring. The first one is to proactively detect outages and performance issues: thanks to continuous checks, the system knows when something stops working or performs below a certain threshold. The second benefit is to efficiently troubleshoot network and application issues by comparing real-time with historical data. With this method, a network engineer can understand whether the network recently changed and that caused the degradation of services and applications.
Active Network Monitoring Tools
Two commands that I always use to illustrate how active network monitoring works are ping and traceroute. Most network engineers are familiar with these tools in their day to day network troubleshooting efforts. Ping reports in real-time how long it takes for a data packet to reach to and return from a remote host or service. Running continuously ping tests will provide round-trip time and packet loss, which are key metrics that impact network throughput and application performance. In the example below, I am running a ping test against google.com:
ping google.com PING google.com (172.217.2.110): 56 data bytes 64 bytes from 172.217.2.110: icmp_seq=0 ttl=117 time=11.889 ms 64 bytes from 172.217.2.110: icmp_seq=1 ttl=117 time=12.204 ms 64 bytes from 172.217.2.110: icmp_seq=2 ttl=117 time=17.930 ms 64 bytes from 172.217.2.110: icmp_seq=3 ttl=117 time=12.286 ms 64 bytes from 172.217.2.110: icmp_seq=4 ttl=117 time=17.963 ms ^C --- google.com ping statistics --- 5 packets transmitted, 5 packets received, 0.0% packet loss round-trip min/avg/max/stddev = 11.889/14.454/17.963/2.854 ms
Traceroute is another utility that can be used to inspect the route that packets traverse to reach a specific destination. The benefit of traceroute is that it can spot the point in the network that is causing traffic congestion.
traceroute google.com
traceroute to google.com (172.217.15.110), 64 hops max, 52 byte packets
1 192.168.0.1 (192.168.0.1) 2.372 ms 2.189 ms 2.347 ms
2 * * *
3 b3328.pitbpa-lcr-21.verizon-gni.net (100.41.133.170) 11.729 ms
b3328.pitbpa-lcr-22.verizon-gni.net (100.41.133.172) 9.240 ms
b3328.pitbpa-lcr-21.verizon-gni.net (100.41.133.170) 8.969 ms
4 * * *
5 * * *
6 0.ae10.gw13.iad8.alter.net (140.222.225.219) 20.913 ms
0.ae9.gw13.iad8.alter.net (140.222.225.63) 12.745 ms
0.ae10.gw13.iad8.alter.net (140.222.225.219) 14.772 ms
7 204.148.79.46 (204.148.79.46) 12.159 ms 12.336 ms 12.462 ms
8 * * *
9 216.239.54.124 (216.239.54.124) 14.704 ms
216.239.49.168 (216.239.49.168) 12.655 ms 13.230 ms
10 108.170.246.49 (108.170.246.49) 14.893 ms
216.239.58.31 (216.239.58.31) 21.749 ms
108.170.246.67 (108.170.246.67) 15.575 ms
11 * iad30s21-in-f14.1e100.net (172.217.15.110) 15.321 ms 12.739 ms
Summary of Network Monitoring Techniques
When managing large and complex networks, SNMP, passive analysis and active monitoring are three techniques all equally important.
| Type | Description | Benefits |
| SNMP | Runs SNMP GETs to collect information about devices’ status and resources | Monitor device status and resources. |
| Passive | Intercepts user traffic for analysis and statistics. | Monitor network usage and user behavior. |
| Active | Runs tests and checks against other hosts in the network. | Test and monitor network resources, services, and applications. |





