Whether you’re looking to monitor an enterprise infrastructure or reduce troubleshooting time, this article will help you evaluate what’s the best network monitoring system that fits your needs. In this article, we’ll review the importance of network monitoring software, the different types of tools available, and what roles each one of them play. These are the basics to implement an effective network monitoring strategy in your organization that delivers true network visibility.
Table of Contents
- What is network monitoring?
- Why is network monitoring important?
- Types of network monitoring tools
- Benefits of network monitoring tools
- Network monitoring tools best practices
- Conclusion
In the last section of this article, we will also provide a brief overview of NetBeez, an active network performance monitoring tool. NetBeez enables network teams to detect network issues fast and reduce troubleshooting time of performance problems.
What is network monitoring?
Network monitoring is the process of verifying the availability and performance of a computer’s network. This task involves the periodic check of the operational status of network equipment like routers and switches, along with the functionality of services and applications. For this reason, network monitoring is a crucial function of a network management system.
The goals of a network monitoring system is to ensure that a network infrastructure functions as designed, reduce troubleshooting efforts, and minimize service downtime. Ultimately, by detecting problems as soon as they occur, network monitoring systems enable organizations to reduce the time to detect and resolve network incidents and performance degradation issues.
Why is network monitoring important?
Network monitoring has several advantages for organizations that operate and support a network infrastructure:
- Availability Monitoring and Fault Detection: Network monitoring tools detect and alert administrators about network outages as soon as they happen. This proactive approach allows quick troubleshooting and minimizes downtime of business operations.
- Network Troubleshooting: Network monitoring systems provide the necessary performance and diagnostic data required to identify the root cause of network issues. NetBeez for example provides information about how many remote network components and locations are experiencing an outage, helping isolate the root cause.
- Performance Optimization: Network performance monitoring helps identify bottlenecks, congestion, and other issues that can degrade the end-user experience. By tracking network traffic and resource utilization, administrators can optimize network configurations to maximize uptime and performance.
- Resource Planning: Network monitoring assists in resource planning by providing insights into current usage trends. This information helps organizations forecast when the network and its systems require upgrades, how to manage capacity, and when to replace the hardware.
- Network Security Monitoring: Monitoring tools are vital to detect unusual network activity or security breaches. By tracking network traffic, network security monitoring tools log and report unauthorized access attempts. Security teams can respond promptly to potential threats and vulnerabilities.
- Compliance and Reporting: Many industries and organizations have specific regulatory requirements for network security and data protection such as PCI and HIPAA. Network monitoring tools generate reports and logs that measure compliance with these standards.
- Quality of Service (QoS) Management: Most organizations support real-time communication services such as VoIP or video conferencing. An effective network monitoring deployment helps ensure that the network has low latency, jitter, and packet loss.
Types of network monitoring tools
There are three main types of network monitoring tools:
Each type has a specific function, set of functionalities, and vendors. Some vendors offer solutions that incorporate all three types of network monitoring, while some vendors specialize in one specific type.
The following table lists the main function and limitations of each type of network monitoring solution.
| Type | Function | Limits |
|---|---|---|
| SNMP | Report the status and performance of network devices, such as routers and firewalls. | Doesn’t capture the end-user experience, but only the status and performance of network devices. |
| Passive | Capture traffic to identify network activity, apps performance, and security incidents. | Reactive network performance monitoring as it relies on real network traffic. |
| Active | Continuous synthetic monitoring to measure end-to-end performance and proactive alert of network issues. | Requires installation of a dedicated hardware or software monitoring agent. |
Small companies that have simple requirements tend to select all-in-one solutions, as they may reduce Total Cost of Ownership and reduce complexity. Medium to large organizations tend to have more complex requirements thus generally select specialized solutions for each category.
SNMP-based tools
The Simple Network Management Protocol (SNMP) is an Internet standard used to request information from a device like a router, switch, firewall, or server, about the status of its resources, such as CPU utilization, memory consumption, and network interfaces. This class of tools is the first one to be developed and introduced in the 1980s to monitor a computer network. As a result, the SNMP protocol is the building block of a network management system. The simple network management protocol well adapts to IT infrastructure monitoring.

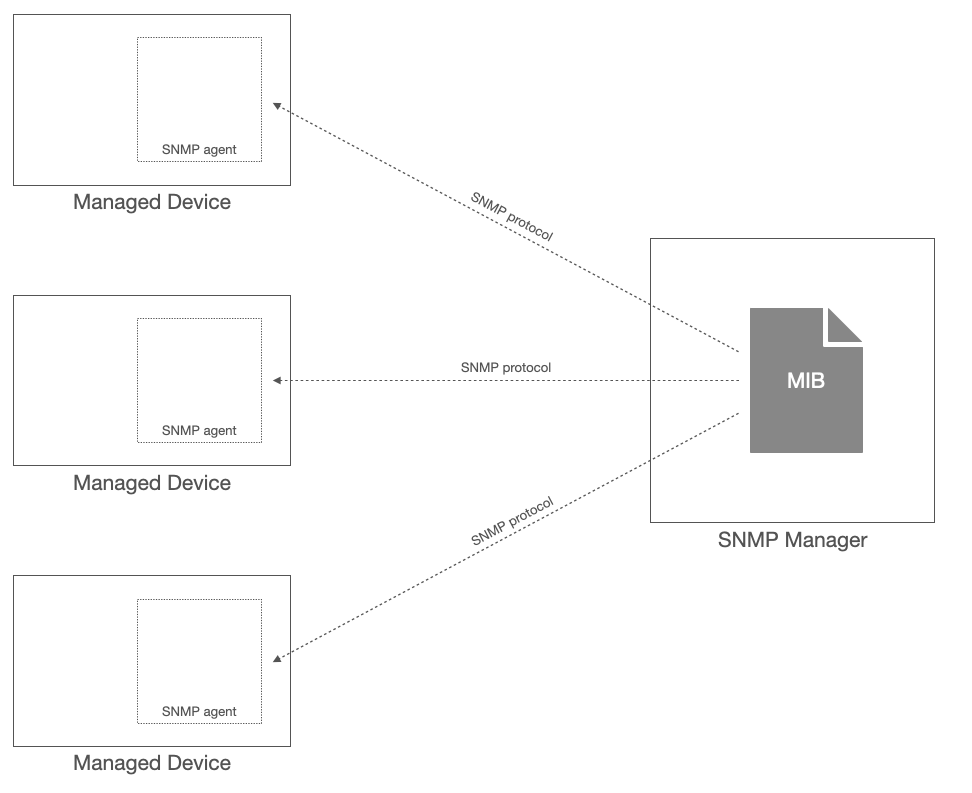
The following diagram represents the different SNMP components of a typical installation.
SNMP components
Managed devices – Any network device that needs to be monitored for availability and performance or managed by pushing configuration requests. Managed devices can be routers, switches, servers, and any appliance that can run an SNMP agent.
SNMP agents – This is the client software that runs on the network component to reports its status and performance data to the SNMP manager. By default, SNMP agents use port UDP 161 to receive requests from SNMP managers. Agents can also send traps to SNMP managers when a certain event happens, such as a failure or a resource crosses a certain threshold. Traps are sent, by default, to port UDP 162 to the SNMP manager.
SNMP managers – These are the servers where the centralized network monitoring process runs. SNMP managers periodically query the SNMP agents running on managed devices. They request data from SNMP agents, process it, and can send commands to alter device settings.
SNMP MIB and protocol
SNMP MIB – A MIB (Management Information Base) describes the data, and defines its structure, that can be queried to an SNMP agent. MIBs organize in a hierarchical way Object IDentifiers (OIDs). Vendors publish their MIBs so that network administrators can import them the SNMP manager so they can integrate it with a specific device. Most vendors typically supports a set of standard MIBs for its nodes. Each vendor can also develop custom MIBs for specific, proprietary functionality. The SNMP MIB provides a method for registering a company’s OID for inclusion into the master MIB tree. For instance, NetBeez’s root OID is 1.3.6.1.4.1.44523.
SNMP protocol – The SNMP protocol has a set of well defined queries that can be exchanged between SNMP agents and managers. For instance, the function snmpget requests information on a network entity with one or more OIDs. The function snmpset sets a parameter on a network entity.
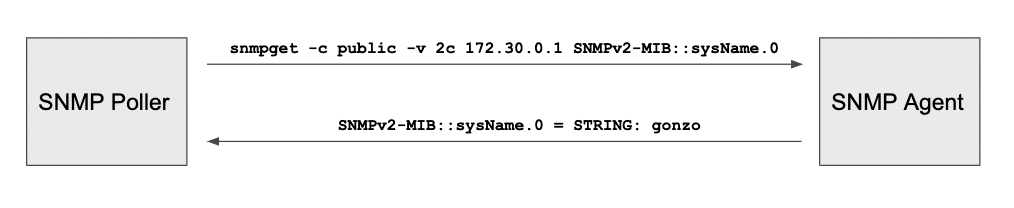
snmpget
The following image shows an SNMP poller (synonym for manager) that executes an snmpget against an SNMP agent to request the managed device’s hostname, which is returned as a string (gonzo). In this case, the MIB named SNMPv2-MIB translates the OID 1.3.6.1.2.1.1.5 with the resource sysName.0 so human can understand what’s the resource queried (this is quite similar to the DNS resolution system).
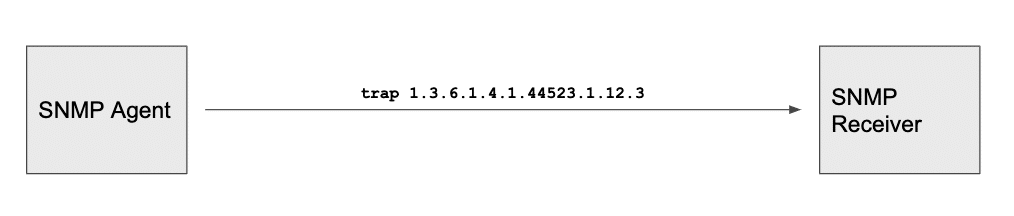
snmptrap
SNMP traps are used to notify the main server that there’s a problem with the network component. The SNMP agent generates an trap to the configured SNMP manager (in this case also called receiver) to alert about a network issue. The OID of the trap is 1.3.6.1.4.1.44523.1.12.3 which is associated with the NetBeez BeezKeeper MIB. As mentioned before, SNMP traps enable network devices to report that something is wrong to an SNMP server, so it can alert the network administrator. In this case the SNMP agent is the NetBeez server reporting an alert.
Passive network monitoring
Passive network monitoring is a technique that relies on intercepting network traffic to identify network activity, links utilization, and application performance. By doing so, passive network monitoring systems can reveal what users, applications, and protocols are generating network traffic. This methodology for traffic monitoring has also application in security and forensics analysis, as it provides a method to intercept traffic. There are three ways to passively monitor a network: network TAP, SPAN port, and flow-based protocols. Let’s briefly introduce each one of them.
Passive network monitoring components
Passive network monitoring systems generally have two main components:
- One or more devices that capture the network traffic to generate flow statistics and bandwidth utilization reports. As we’ll see in the next section, there are three main types of capture devices: Network tap, SPAN ports, and flow protocols.
- A collector server that stores the data for historical analysis and runs the management and reporting dashboard. Here is where the main network monitoring process runs. In the case of large deployments, collectors may scale into multiple hosts with hierarchical architecture where a master node orchestrate one or more child nodes.
Collectors
There are three main types of devices that collect passive monitoring data (packet sniffing):
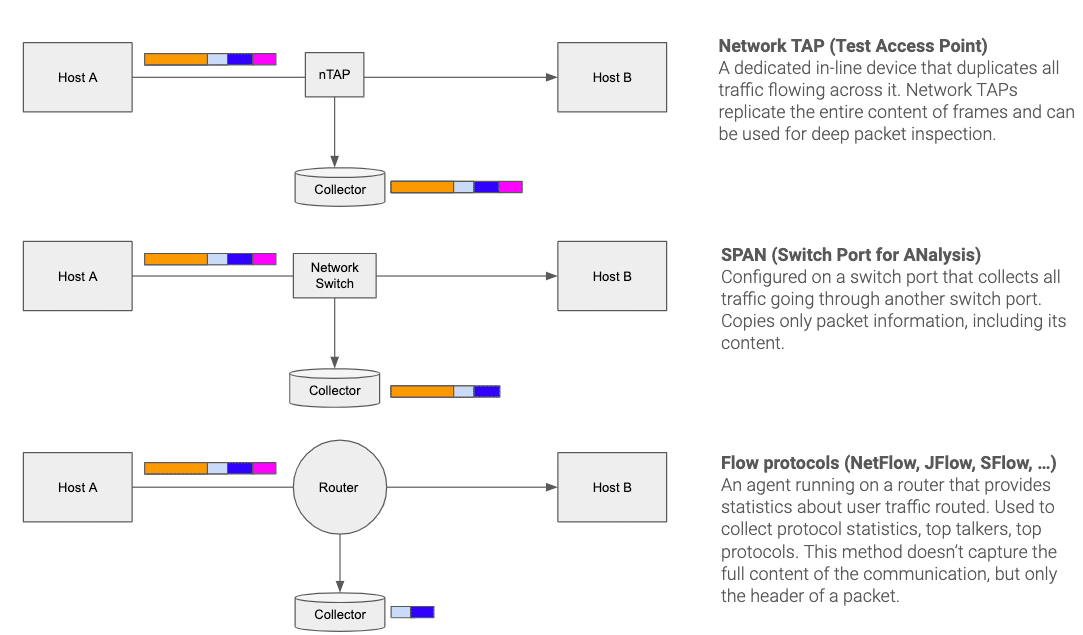
Network TAPs are dedicated devices that are installed in-line where the traffic has to be analyzed. A network TAP replicates the entire content of the frames (layer 2) flowing across. For this reason, network TAPs are the best options for deep packet inspection. Many SIEM (Security Information and Event Management) tools adopt this technology to proactively identify and mitigate potential security threats or breaches.
SPAN (Switch Port for ANalysis) ports are configured on a switch by instructing it to send a copy of the traffic from a specific port or VLAN to another port on the switch itself or on another switch that has been connected to a network collector. SPAN ports are able to copy the entire packet, including its payload.
Network devices that generate flow data and analysis. Flow data is generated by sampling network traffic and extracting certain information from it. This type of passive analysis doesn’t capture the full content of a packet, but just its header, so it’s mostly appropriate for protocol and traffic statistics.
The following picture represents the three different types of passive monitoring for packet sniffing: Network tap (top), SPAN port (middle), and flow protocol (bottom).
Common flow protocols
Cisco released the first version of a flow protocol in 1996 with NetFlow. Since then, several proprietary and open protocols have been developed. The most important ones are:
- NetFlow – This proprietary protocol by Cisco is currently on version 9. Netflow provides different statistics about the traffic captured, mostly at the network (layer 3) and transport (layer 4) level. By default, NetFlow records are sent to a collector via UDP port 2055.
- SFlow – This industry standard protocol stands for “sampled Flow” and allows network routers to send flow statistics from the data link (layer 2) to the application (layer 7) level. For this reason, SFlow has applications in MPLS and other “layer 2.5” networks. Many networking vendors, such as Alcatel-Lucent, Arista, Cisco, and Extreme Networks, support SFlow.
- IPFIX – IPFIX, which stands for “IP Flow Information Export”, is a standard-based protocol (RFC 3917) that was created to export IP flow data from network devices like routers and probes. IPFIX integrates with accounting and billing systems as well as network management systems.
- Jflow – Proprietary protocol developed by Juniper Networks for their network management software.
- CflowD – Proprietary protocol developed by Nokia for their network management software.
Active network monitoring
Active network monitoring software generates synthetic network and application transactions to verify the correct functioning of a computers’ network, including its services and applications. Unlike passive monitoring, which captures network traffic as it flows, active monitoring continuously injects test traffic in the network to assess its performance. For this reason, by continuously testing the network, its services, and applications, this method provides quick detection. In many situations, active network monitoring helps identify potential issues before they impact users or services.
Active network monitoring architecture
Active network monitoring tools are composed by a set of distributed agents managed by a central server. The central server hosts the database and the dashboard. The remote agents runs the performance tests, collect the tests’ results, and send the data to the central server. The central server analyzes the metrics, computes baselines, generates alerts, visualizations, and notifications. Differently from SNMP tools, in which the server does the monitoring, in active tools the agents monitor the network, its services and applications. For this reason, active network monitoring is a type of distributed network monitoring as it relies on several vantage points.
Active network testing
Active monitoring software employs software agents or hardware sensors to provide real time network testing. The network administrator installs the agents in strategic points of the network, including users’ laptops and desktops. Active tests report real time network monitoring data such as end-to-end connection, packet loss, jitter, bandwidth, DNS and HTTP response time. Specialized wireless sensors retrieve even more data about enterprise WLANs, such as WiFi connection timing, association, and authentication failures.
Common Metrics Tracked
The following table reports some of the key features of NetBeez, an active network monitoring solution.
| Test Name | Performance metrics |
|---|---|
| Ping (ICMP) | Round-trip time, packet loss, jitter, MOS |
| DNS | Resolution time, failure rate |
| HTTP | Response time, failure rate of the hypertext transfer protocol (HTTP) |
| Traceroute | Per hop routing information: Round-trip time, MTU |
| Path Analysis | Network topology information: Round-trip time, ASN, geolocation |
| Iperf | Bandwidth, packet loss, jitter |
| Network speed | Download, upload, and latency |
| VoIP | MOS, packet loss, jitter, latency |
Benefits of network monitoring tools
SNMP benefits
Benefits of SNMP-based network monitoring solutions include:
- Simplicity: SNMP has a simple client-server architecture that is easy to understand and straightforward to implement. That doesn’t necessarily mean that all SNMP tools are easy. Considering the ease of setup should be evaluated during the trial phase.
- Device and Availability Monitoring: SNMP provides visibility into network device status and performance, enabling quick alerting upon failure or performance issues of a computer network. A network device can also be a web server but also access points, storage devices, etc.
- Scalability: In general, SNMP can scale to accommodate networks of varying sizes, from small local networks to large enterprise infrastructures. Scalability may also be a function of the number of servers required to monitor an infrastructure (horizontal scaling).
- Interoperability: SNMP is vendor-agnostic, allowing it to work with a wide range of network devices and manufacturers.
Passive monitoring benefits
The benefits of passive network monitoring software are:
- Traffic Monitoring and Diagnostics: Since passive monitoring captures real network traffic, it can be used as a microscope to diagnosing network issues. In fact, network admins can capture any packet that flows through a link, and that gives full visibility. This makes it very helpful to troubleshoot problems with applications’ transactions, wireless drivers, and specialized hardware that has a network interface and custom TCP/IP stack. To conclude, we consider this network troubleshooting method more a reactive one than a proactive one.
- Capacity Planning: Passive monitoring tools analyze traffic patterns over time, allowing to identify the top traffic originators in terms of hosts, network locations, and applications or protocols. This information helps organizations plan for future network capacity needs. By understanding current usage trends, administrators can make informed decisions about scaling the network infrastructure to accommodate growing demands.
- Detection of Security Threats: By observing normal network behavior, passive monitoring can easily detect anomalies or deviations from the baseline. Unusual patterns in traffic, unexpected data flows, or irregular protocol usage can indicate security threats, such as Distributed Denial-of-Service (DDoS). This visibility enables timely responses to potential breaches. In the event of a security incident, passive monitoring data can also serve as a valuable resource for forensic analysis.
Active network monitoring benefits
Benefits of active network monitoring include:
- Quick detection of network problems – By constantly running tests that verify network availability and applications performance, active network monitoring can detect issues fast. This real time network monitoring technique adds extra network visibility to SNMP and passive analysis tools, as it alerts about network outages that happen within an unmanaged network environment, such as the Internet.
- Continuous performance measurement – Since active network monitoring keeps generating network traffic, it continuously computes network performance metrics such as bandwidth available, response time, and packet loss. Differently from passive analysis, which only measures performance when there’s actual user traffic, active network monitoring provides a better baselines as the measurements are 24x7x365.
- Service assurance – Active monitoring helps organizations track and meet SLA (Service Level Agreements) commitments by continuously assessing network performance against agreed-upon benchmarks. Real time network monitoring can detect performance degradation issues, allowing swift corrective actions.
- Monitoring of third party networks and services – This is a key benefit of active network monitoring. SNMP and passive tools can only monitor internal networks because they either require access to the network devices or the installation of a physical probe. Differently from those tools, active ones can also monitor third-party networks and services. Take the example of measurements like traceroute or path analysis.
- Digital experience monitoring – Active tools provide a way to analyze the end-user experience with digital services, SaaS applications, websites, and other online assets. By monitoring various metrics such as page load times, transaction success rates, and error rates, organizations can optimize their digital services, enhance user satisfaction, and troubleshoot user complaints.
Network monitoring tools best practices
The network monitoring tools market is one of the most competitive in IT. The Stanford Linear Accelerator estimates that exist more than 700 network monitoring tools. For this reason, when shopping for a tool, it’s important to have a good idea on what are the requirements that needs to be prioritized. The following functionalities are some things to consider when evaluating network monitoring solutions.
Polling frequency
Polling frequency determines how often the data is fed into the network monitoring server for alert processing and real time visualization. The shorter the polling interval and the faster the detection of incidents or potential network issues.
Data Granularity
This determines how fine grained is the availability and performance data that is available on the monitoring dashboard. When troubleshooting performance anomalies, pick raw data rather than sampled data as it provides better visibility into performance changes. Granularity helps cutting troubleshooting time.
Data retention
Data retention is another important factor for historical performance analysis. Generally, data retention is a function of the type of data that needs to be stored and the amount of storage available. For instance, SNMP data and performance metrics obtained with active network monitoring require less space per data point than a full packet capture. As a result, passive tools typically have a shorter data retention span due to the amount of data collected. Another factor to consider is whether the tool is hosted by the vendor (e.g. SaaS) or self hosted. In SaaS tools, there’s less flexibility in the configuration of the data retention period because it’s hosted by the provider. For this reason, it’s important to pay attention to what’s included in a plan.
Alerting profiles
It’s important to consider what type of failures are detected by the alert profiles. Most of tools can customize alert rules and send notifications about certain problems occurring within the network, applications, or services monitored. The alerts can be displayed in the dashboard or propagated via email or other mean to the appropriate recipients or systems.
Scalability
For medium and large network environments, scalability is a mandatory requirement. If a tool doesn’t scale, network admins won’t be able to monitor the entire network. For example, when evaluating an SNMP tool, it’s very important to factor what’s the maximum number of devices supported. In the case of a passive network monitoring solution, it should be evaluated what’s the data rate that the collector can ingest. Lastly, for active network monitoring tools, review the number of agents that can be managed, as well as the number of tests results that can be processed every second.
Interoperability and integrations
A monitoring tool is an essential network management component that is integrated with other systems and applications to exchange or correlate relevant data. This include ticketing systems, other types of monitoring tools, logs processors, accounting tools, etc. For this reason, tools should not only support standard protocols such as SMTP, SNMP, and syslog, but also integrations with third-party tools.
Deployment options
Some network monitoring tools can be hosted on-premises, others are purely SaaS based, others support either on-prem or SaaS. When thinking about where a monitoring tool should be hosted, it’s important to consider the price, ease of management, security, and regulatory requirements (in the case some of some industries where data location is enforced).
Complexity
Usability and amount of training required will impact the effectiveness of the tool. Adopting a solution that requires long extensive training and that few users have the ability to manage and use, will diminish the value of this tool. When other features are equal, pick the tool that has the simplest and easiest interface.
Other factors left out in this analysis include the technical support model, the licensing terms, and the platforms supported.
Network performance monitoring with Netbeez
NetBeez is a Network Performance Monitoring (NPM) and performance testing solution designed to help modern enterprises ensure the reliability and efficiency of their computer networks. It provides real time insights into network performance by actively monitoring the network from the end-users’ perspective. This is done by deploying distributed agents that run end-to-end continuous tests to other hosts, NetBeez agents, or applications. Agents support on-premise and hybrid environments to get the view of the entire network.
Setting up monitoring with NetBeez requires few simple steps by the network administrator. If you don’t have a dashboard, go to the NetBeez homepage and request a demo or free trial. Once you get your dashboard, follow the onboarding process.
Deploy network monitoring sensors
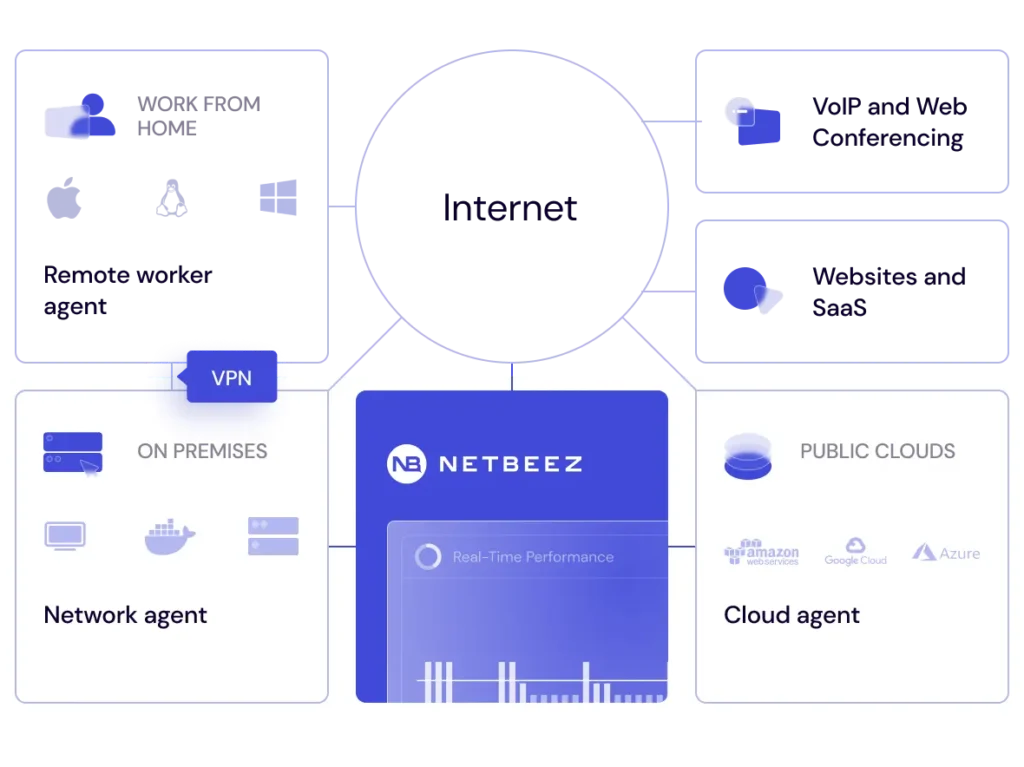
Install the NetBeez agents at the network locations and on the end-user devices you want to monitor. Follow the installation instructions from the online documentation. NetBeez provides two types of complimentary monitoring options that extend network visibility beyond the corporate premises:
- Network Agents are hardware, virtual or software appliances that get installed on-premise at remote branch offices, public clouds, and data centers. The data collected by these units will help you capture the remote network experience. For instance, if all the agents find performance issues with an application, then the root cause most probably lies with the application provider network. On the other hand, if only one agent reports performance problems, it could reveal a local network problem.
- Remote Worker Agents are software clients for Windows or Mac operating systems. The data collected by these units include resources, such as cpu utilization and wireless networks metrics, as well as network and application performance tests. Complementing this data with that from network agents will help you compare the end-user performance, and identify the root cause of end-user experience issues fast. Bottom line, these agents are vital to monitor the network of work from home and remote employees.
Select what targets to monitor
Go to the Targets tab and create targets. NetBeez provides three types of targets to monitor:
- SaaS are any third-party hosted applications such as MS Office, Zoom, or Salesforce.
- Target template, such as a website, a VPN connection, a local gateway, and a DNS service.
- Custom target, any service or application that needs performance and availability monitoring.
Setup alerts, emails, and notifications
In the Anomaly Detection section of the NetBeez dashboard, the administrator defines the alerts profiles and the notification methods. By default, NetBeez generates alerts when a target is unreachable or when a performance degradation occurs. Notifications enable network admins and support teams to get an email or a page when this happens.
NetBeez supports sending notifications via standard protocols, such as SMTP, SNMP, and syslog. It’s also possible to use webhooks for automation and out-of-the-box integrations. NetBeez has integrations with Azure AD, ServiceNow, MS Teams, Slack, PagerDuty, …
Lastly, NetBeez also provide a json-based API interface that organizations can use to build custom dashboard for their needs. For example, Internet Service Providers could also implement a service status dashboard on a standard web server so their subscribers can track network downtime.
Key features
- Active Monitoring: NetBeez actively tests network connectivity, routing, application performance, and end-user experience by simulating user interactions with applications and services. Traceroute and path analysis are available to discover the network topology.
- Distributed Agents: NetBeez uses distributed agents placed strategically within a network. These agents continuously monitor network performance data from different locations, providing a comprehensive view of the network’s health. NetBeez also offer wifi sensors to monitor a wireless network.
- Real-Time Alerts: The platform generates real-time alerts when it detects network problems, allowing IT teams to respond to issues fast, minimizing downtime and user disruptions. The user can define alert profiles based on up-down detection, performance baseline, or threshold based.
- Historical Reporting: NetBeez offers historical reporting and analytics, with data retention up to 2 years. As a result, the extended data retention enables IT administrators to analyze network downtime performance trends over time. This data helps in making informed decisions for network optimization and capacity planning.
- Multi-Platform Support: NetBeez supports various platforms and devices, allowing businesses to monitor network performance across different environments and operating systems. The network monitoring agents can be Ethernet, Wi-Fi, virtual, and Docker-based appliances or Windows, Mac, and Linux software clients. The server can run on-prem or hosted in the cloud.
- User Experience Monitoring: NetBeez focuses on monitoring user experience, providing insights into how end-users are experiencing network services and applications. This user-centric approach helps in identifying and addressing issues that directly impact users.
- API for Custom Dashboards: NetBeez provides a JSON API and webhooks to integrate with third-party tools, and build custom dashboards.
Use cases
- Digital Experience Monitoring: Analyze the performance of digital systems and services by tracking the digital experience from the end-user perspective.
- Network Performance Monitoring: Run continuous, end-to-end tests to ensure the network infrastructure well performs, proactively identifying and resolving issues.
- Remote Worker Network Monitoring: Extend network performance monitoring to the home office with Windows and Mac endpoints.
- WiFi Monitoring and Assurance: Monitor a 802.11 wireless network from the client perspective to deliver reliable and secure wireless connectivity.
- Hybrid Cloud Network Monitoring: Ensure connectivity, performance, and reliability of your private and public cloud networks.
- SaaS and Application Performance Monitoring: Verify the end-user experience and performance of SaaS and hosted applications.
Conclusion
Network monitoring enables organizations to detect and troubleshoot network outages and performance problems that impact business operations. There are three main categories to keep in mind: SNMP, active, and passive. Network administrators responsible for operating and supporting an infrastructure needs to understand the best practices of network monitoring. NetBeez is a network monitoring tool that offers a simple way to verify performance and availability of enterprise networks. Tailored for modern enterprises, NetBeez supports hybrid environments, including corporate WLANs and work-from-home users. If you are in search for network visibility, sign-up for a free trial, or request a demo.





