Ping is a command line utility that verifies the reachability and round-trip time (RTT) to a destination TCP/IP host. This command uses the Internet Control Message Protocol (ICMP) “echo request” (Type = 8) and “echo reply” (Type = 0) messages to return such information. Along with traceroute, is one of the most used commands used to troubleshoot IP networks.
Ping on Windows
Microsoft’s native ping utility has changed from operating system version to version. I will use the ping command in Windows 7 and cover some of the options I use and why.
ping [-t] [-n count] [-l size] [-f] [-i TTL] [-w timeout] target_name
I like to point out that the default payload for Microsoft’s ping is 32 bytes and I encourage technicians to use payload sizes that better represent application payload sizes.
In the ping below, you can see a 25% increase in round-trip time latency by simply changing the payload size.
C:\Users\tony fortunato>ping thetechfirm.com Ping statistics for 74.208.236.106: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 56ms, Maximum = 57ms, Average = 56ms
C:\Users\tony fortunato>ping thetechfirm.com -l 1200 Ping statistics for 74.208.236.106: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 74ms, Maximum = 76ms, Average = 75ms
Don’t Fragment (DF) Option
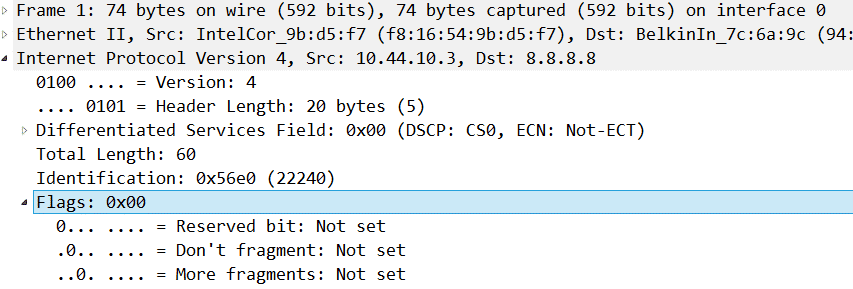
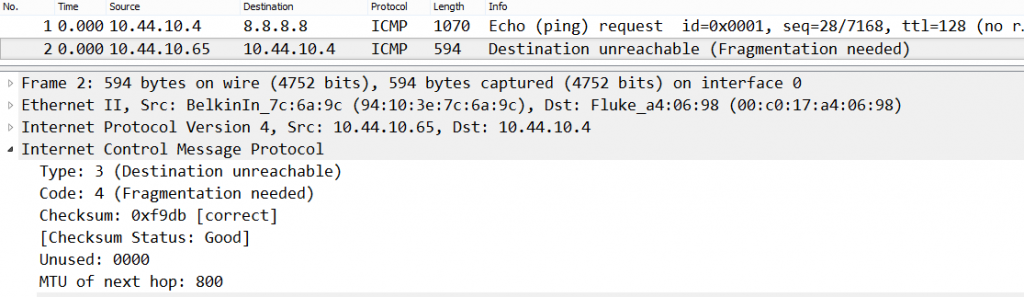
When reviewing ping results, you want to see consistent values as much as possible. My rule of thumb is, “results become less consistent with the addition of more equipment and distance”. Fragmentation issues are always tricky to troubleshoot. I can’t stress enough the importance for you to figure out if your protocols allow fragmentation or not. The process to figure this out is pretty straightforward; capture a packet and look in the IP header to see what the “Don’t fragment flag” is set for. In the screenshot below, the Not set means that the packet allows fragmentation. Don’t forget to check in both directions and as close to each device as possible.
Maximum Transmission Unit (MTU) Option
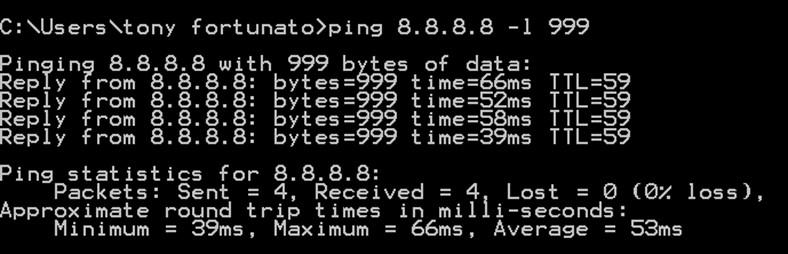
If you want to test for fragmentation issues or just determine what your maximum MTU is, use the –l option and capture/review those ping packets. In the screenshot below, I pinged using a payload size of 999 bytes.
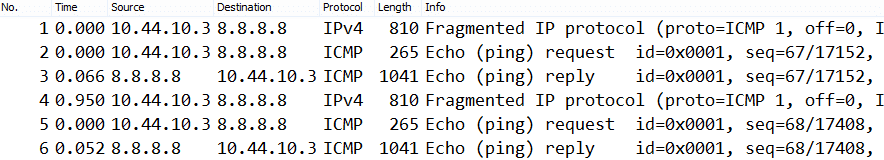
When I reviewed the trace, I can see that my packets were fragmented into 2 packets.
If I was to repeat the same test with a Do Not Fragment Option -f, I would get a different response:
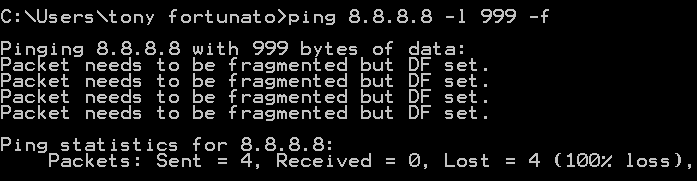
The trace file identifies the supported MTU and who reported it. This is where things can get confusing. If a network device or firewall was blocking ICMP, this ICMP packet would never make it back to the client.
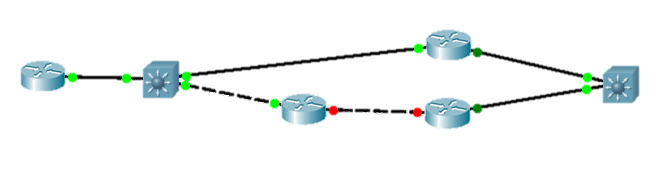
Time To Live (TTL) Option
The Time To Live Option (TTL) is very helpful when you want to determine if the number of hops are increasing or changing. For example, in the diagram below, you might want to ensure that the path isn’t reverting back to the extra hop.
Other ping options worth looking for in your favorite ping tool; GUI, ping interval, size sweep, reporting and QOS options. For Microsoft operating systems, I like to use hrping since it is maintained, portable, and offers these additional options. Here are some of the extra options when you type hrping at the prompt:
usage: hrPING [options] host Data options: -v TOS Type Of Service (default 0, deprecated) -L [s1[:s2[:i[:c]]]] IP datagram size (payload size + 28, default 60) [with sweep] -M Send ICMP timestamp requests -u [port] Send UDP packets (port 7 by default) Operational options: -s time Sending interval between packets in msec (default 500) -c [num] Concurrent sending of up to <num> pings at a time (default 1)Output options: -F file Log output into <file> as well, even if -q is set -T Print timestamp in front of each line -q [r|e|t]Be quiet (-qr=no replies, -qe=no errors, -qt=no timeouts) -y [sec] Print summary of the last <sec> secs (default 10) -g –G Show graph (-gg=close graph on exit, -G use running grping.exe) -? –h This help (-??=more help) Output options: -F file Log output into <file> as well, even if -q is set -T Print timestamp in front of each line -q [r|e|t]Be quiet (-qr=no replies, -qe=no errors, -qt=no timeouts) -y [sec] Print summary of the last <sec> secs (default 10) -g –G Show graph (-gg=close graph on exit, -G use running grping.exe) -? –h This help (-??=more help)
Ping of Death
In the mid 1990s the “ping of death” appeared. In summary, malicious hackers used ping to crash or reboot remote systems by sending an echo request packet with a payload size larger than the standard 56 bytes. This was the first nail in ping’s coffin. Since then, ping and ICMP have been used for floods, attacks, and tunneling, which led to many system admins to simply block all ICMP.
Closing Remarks
Ping is a command-line utility that network engineers use to verify if a device is reachable or not . Back in the day, equipment failure was very common. I chuckle thinking back at those sales people that used Mean Time Between Failure to sell their equipment. As network analysts, we needed a way to see if our hardware or equipment failed and ping did the trick.
Over the years, SNMP was introduced to aid in network visibility, but we still use ping for simple up and down checks. In the 90s bandwidth limits were becoming an issue. The ping response time results could determine if a device or link was causing network slowness.
Back to troubleshooting, wherever possible, I still use ping since there are many things we can figure out to aid us in resolving issues or conducting an application baseline. I always keep my eyes open and test new utilities all the time. I also test utilities to ensure they work as advertised. Whether the software is free or paid, I make sure that it works as advertised. Packet loss will affect your application negatively as much as latency will.