NetBeez and Nutanix Flow Zero Trust Infrastructure
I have been fortunate enough to see NetBeez grow from the initial focus group and release using Raspberry Pi’s, to becoming a complete network and infrastructure analytics tool for the core datacenter to edge users in the work from home world. Taking networking monitoring above and beyond traditional SNMP traps to give a user perspective of your environment is critical in network and infrastructure management as well as providing additional resources in troubleshooting.
In this post I have decided to take advantage of NetBeez’s ability to deploy agents in software to test my micro-segmentation policies using Nutanix Flow in AHV. NetBeez agents provide a great way to deploy a few agents, allowing me to create a nice test bed, with limited resources on my NUC. Nutanix Flow allows end users to create a complete zerotrust environment within the Native Open vSwitch without deploying an SDN solution with a complex overlay underlay network. This means true 1-click provisioning! This blog conveys the simplicity of deploying both solutions to create a zero-trust environment, monitor application traffic, and simulate traffic through applications.
NetBeez and Nutanix Setup
For my testing I was able to deploy 4 lightweight NetBeez software agents via an OVA utilizing Nutanix OVA deployment functionality released in AOS 5.18.
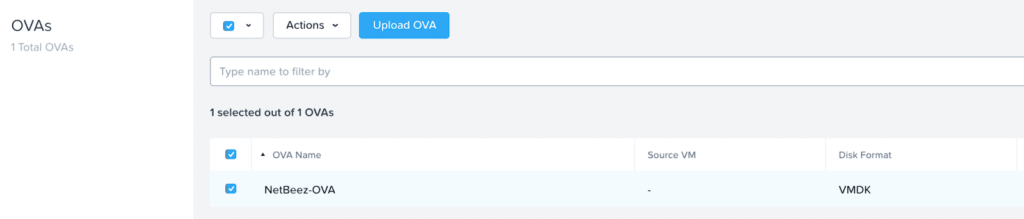
Deploying the agents as an OVA on Nutanix allowed me to not only deploy the VM with “1-Click”, but also to apply the categories per my security policies, set the specs for vCPU and memory, and Prism Central automatically powered on the VM! Once the VM is created with the appropriate category it is added to my security policy and my security posture is added to that VM/Agent.
To take a quick step back, in Prism Central 5.5, Nutanix defined the idea of categories which are key value pairs in which Prism Central can apply a number of policies and native services to these categories from security to disaster recovery.
Deploying my “Applications”, Creating Targets, and Applying Flow Policies
Deploying the NetBeez agents and connecting them to the NetBeez Dashboard was simple and took a few minutes per agent from OVA deployment to monitoring. Once I ran the script from the dashboard my agents were online, and I was ready to create Targets between the “Applications”. I created a simulated application stack with a “SQL” server and “WebApp” using my Linux agents on Nutanix AHV, as well as 2 user groups: Marketing and Developers.
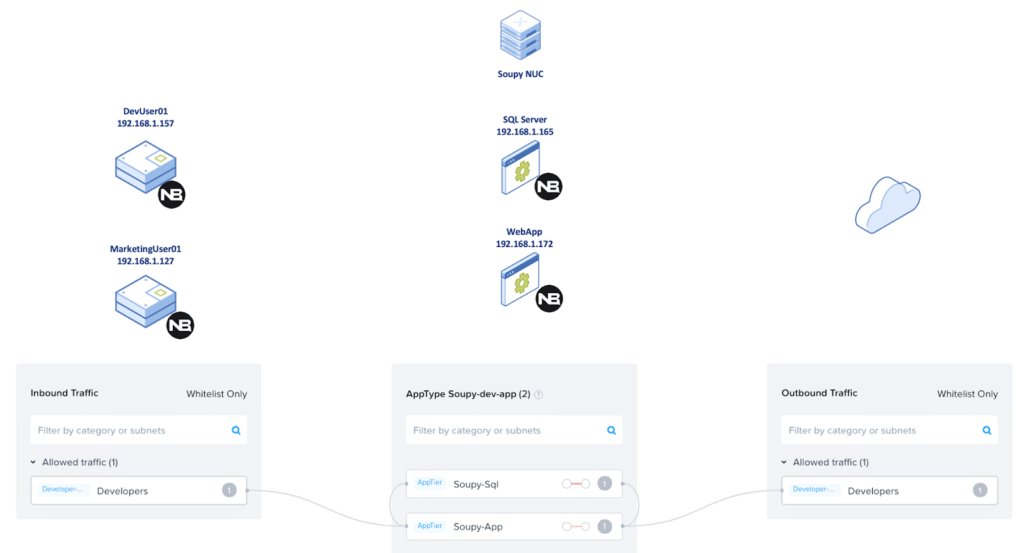
Figure 1
In figure 1 above there are three columns. The first column shows the user groups which simulate my inbound traffic. The one in the middle represents the application stack which simulates the SQL server and WebApp.
Finally, the last column is all of the outbound traffic that is going to the web or internal hosts within my home network. I was limited to the 4 agents listed below in Figure 2, on my Intel NUC running Nutanix Community Edition 5.18. That was still enough for me to simulate a total working environment due to the limited resources.
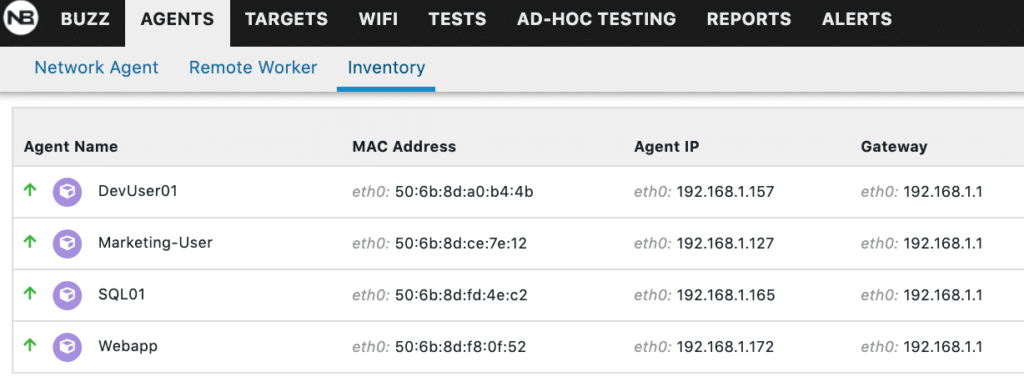
Figure 2
Creating Categories Per my “Applications” and Creating a Security Policy
The categories constructed within Nutanix use key value pairs to allocate entities within the Platform to apply policies such as security, disaster recovery, and more. In my example, I have updated the following drawing to indicate the AppType of Soupy-Dev-App in the center of the drawing and we will apply intra-application policies between the SQL Server and WebApp using AppTier categories. On the left you can see the inbound traffic which will be defined by the two user groups: Developers and Marketing. The Developers will be able to communicate with both the SQL Server and the WebApp, while the Marketing users will only be able to connect to the WebApp. All Outbound traffic is destined to the web and internal devices, which will be addressed later in the blog.
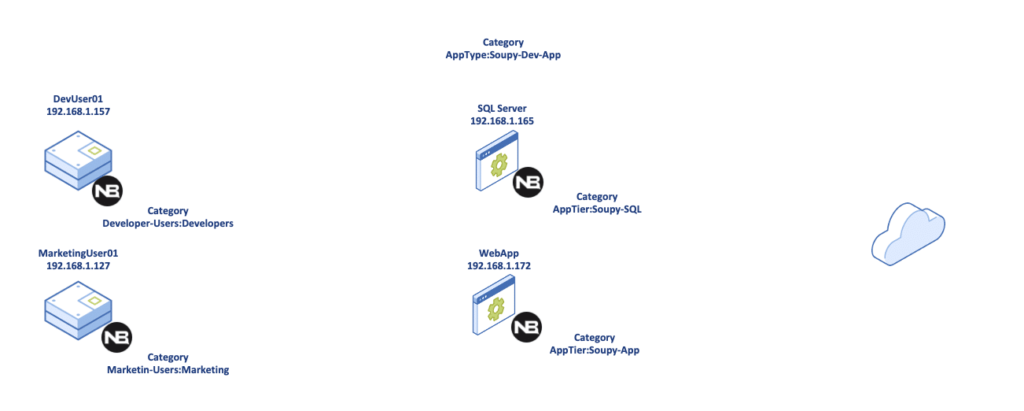
Figure 3
Above in Figure 3, I have created a security policy in the Nutanix environment utilizing the native in platform microsegmentation application called Flow. The policy has been placed in monitor mode which allows me to see all the traffic that is inbound and outbound of the application prior to applying it so I do not black hole any critical traffic such as DNS, Gateway access, etc. In creating my security policies, I select the inbound category of developers, and click the pencil next to the Soupy-Dev-App category in the AppTier and included all HTTP traffic as shown in Figure 4.
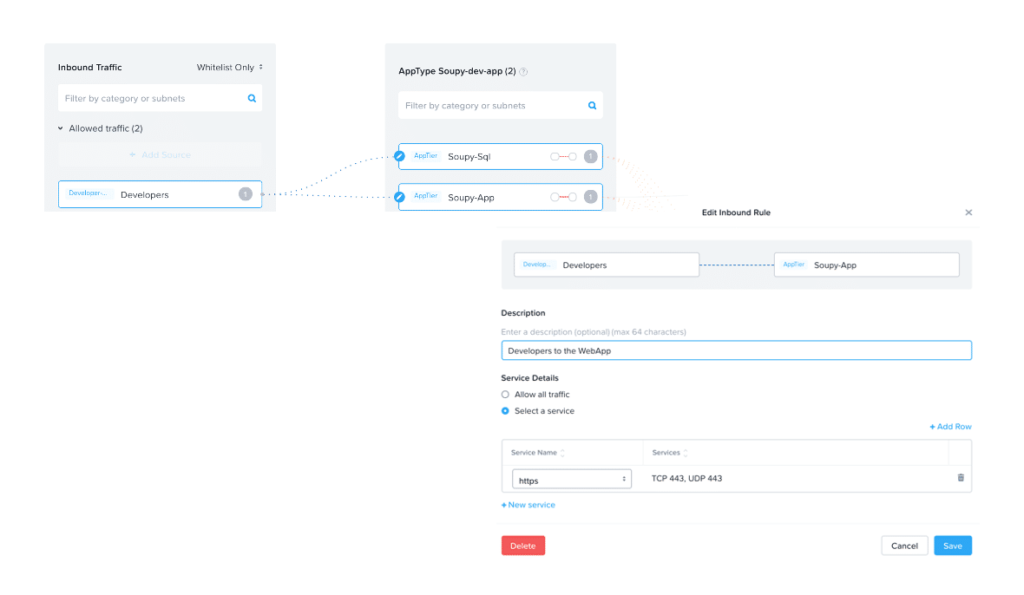
Figure 4
As you can see in Figure 5 below, Nutanix Flow will discover inbound and outbound traffic that users may or may not have included in the security policy. The outbound discovery below indicates for example, 192.168.1.1 as the default gateway of my home network as well as the google DNS at 8.8.8.8.
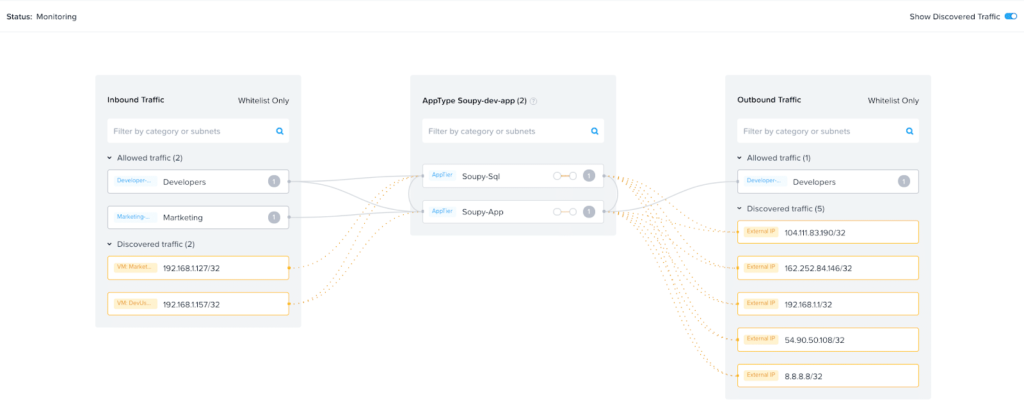
Figure 5
Prior to applying my policy, I checked my NetBeez Cloud Dashboard and I can see the tests that I have setup for ping, http, and traceroute are currently all green. Which means that every application in my environment can communicate with each other as well as externally. I did a mouseover on the Marketing User Agent SQL to show the successful test below in Figure 6.
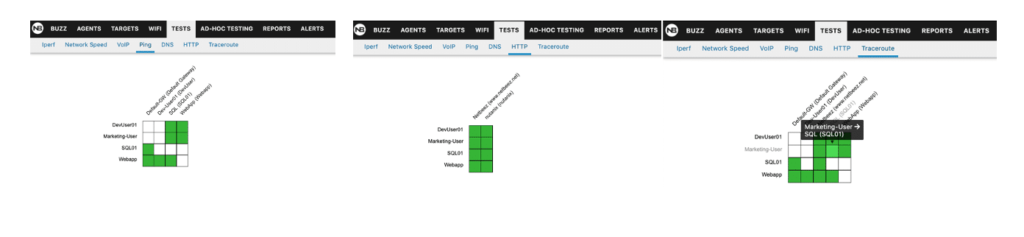
Figure 6
Applying the Security Policy
Since I have created the security policy, using our NetBeez Agents and Cloud dashboard we can validate that we are blocking the proper traffic and the applications can communicate with hosts inside and outside of the network which we need them to on the proper ports. By limiting the open ports our applications are permitted to communicate through, I have created a zero-trust environment. To apply the policy, in Prism Central within the security policies construct, you can right-click the policy and click “Apply” as shown below in Figure 7.
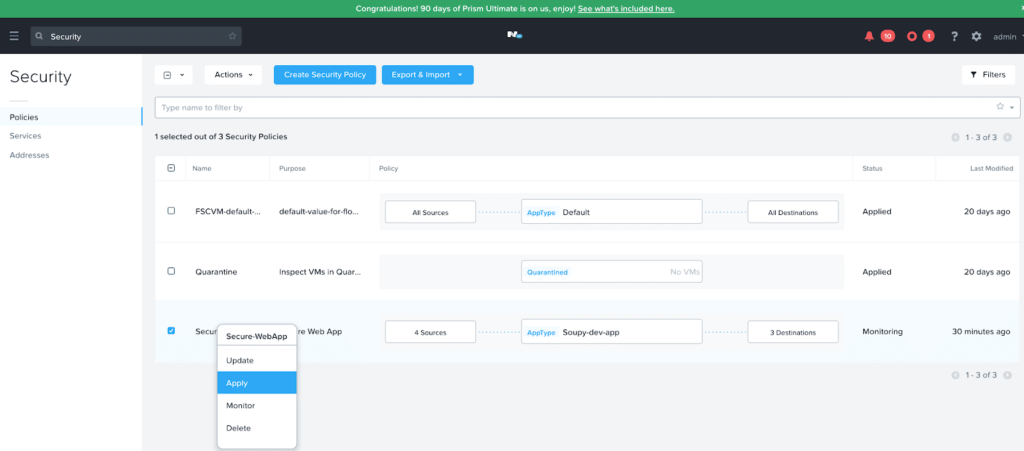
Figure 7
Once the policy was applied, I lost connectivity to the SQL and WebApp Agents. If we look back at our discovered traffic above in the post, we see that outbound traffic discovered our default gateway, DNS, and the IP Address for the NetBeez Dashboard as seen below in Figure 8.
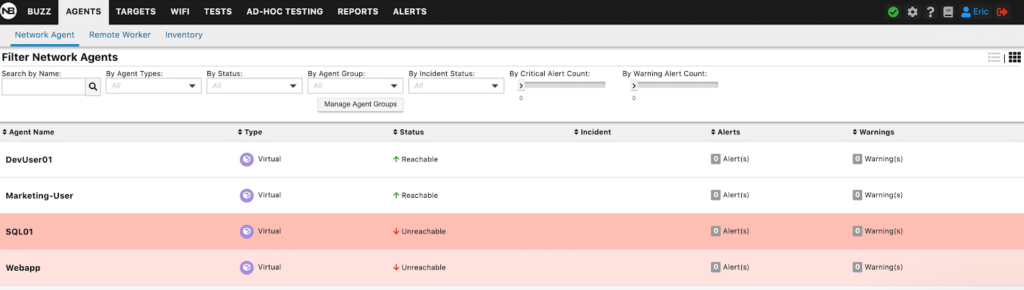
Figure 8
To fix the policy, we simply go into the security policy, mouse-over the entity which we need to add, and add the discovered flows to the policy as seen in Figure 9.
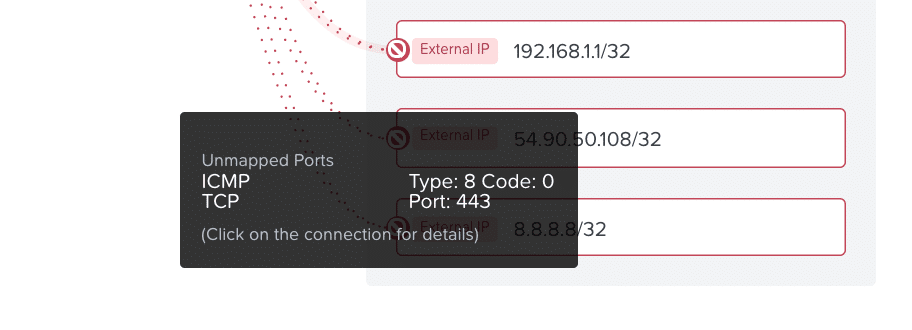
Figure 9
Once we accept the discovered network flows the agents are back up in the NetBeez dashboard. I can see the agents are back up and are blocking traffic originating from the marketing users over TCP port 443.
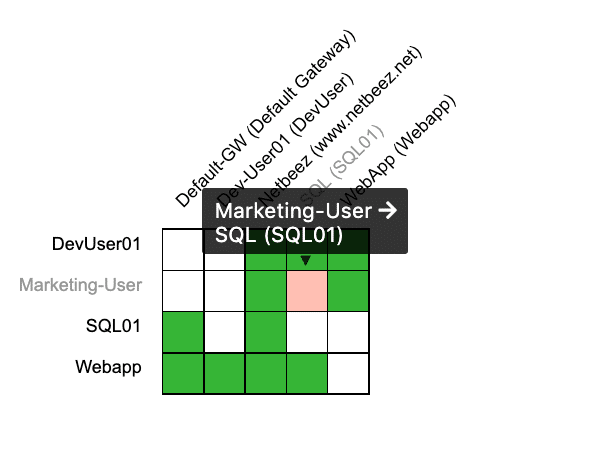
Figure 10
The policy is also blocking external websites (www.netbeez.net and www.nutanix.com) as these destination IP Addresses are blocked outbound from the AppTier, while the User Agents have external access.
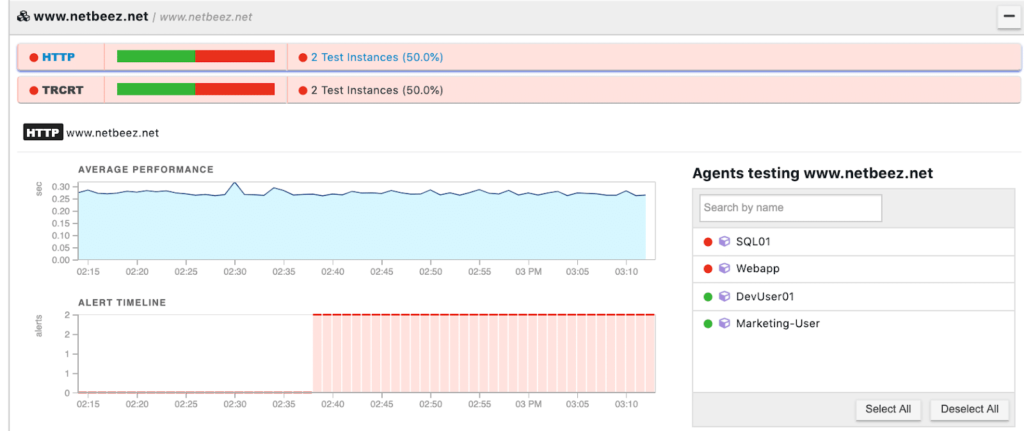
Figure 11
Testing the Policy
With our policy completely up and online and only allowing the inbound and outbound traffic necessary to the communication of the users and application stack we can do some additional testing using the NetBeez Ad-Hoc testing tools. For the purposes of this test we will run an iPerf test from the Marketing User Agent to the SQL Server Agent shown below in Figure 12.
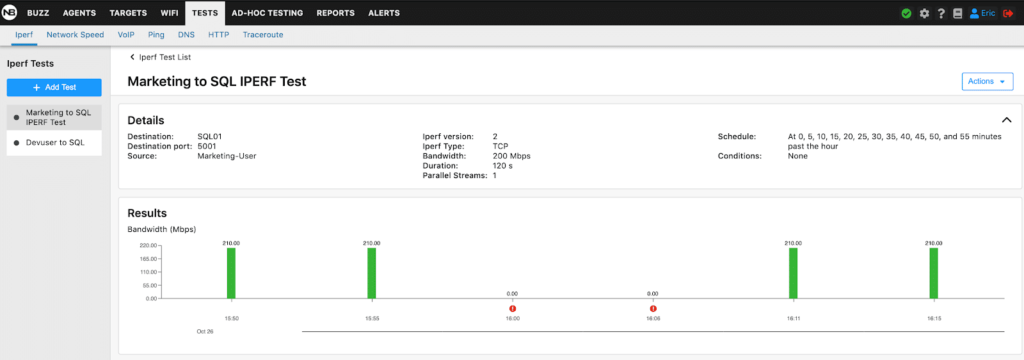
Figure 12
Within a few seconds Nutanix Flow has discovered the traffic on port 5001 from the Marketing Agent shown in Figure 13.
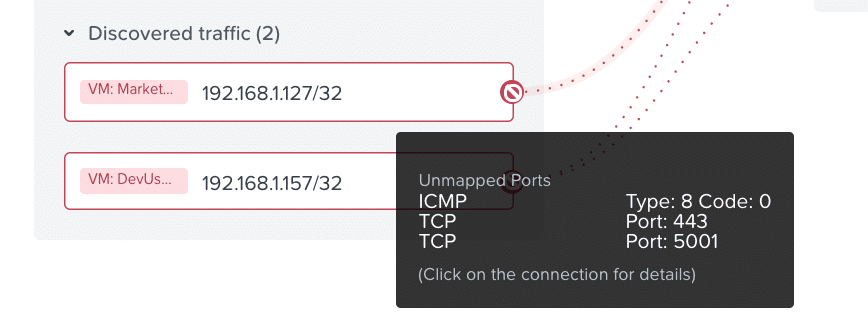
Figure 13
If we mouse-over the traffic and accept all mapped traffic it will also allow the marketing users to communicate over all ports which violates our policy.
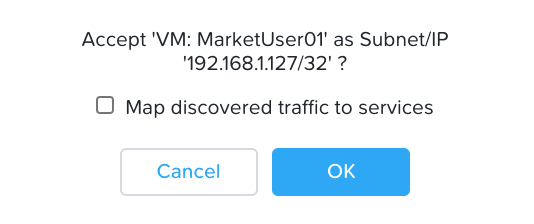
Figure 14
In order to limit the traffic in the policy we only want to add the iPerf traffic on port 5001 as listed above in Figure 14. To simplify this for the purposes of using NetBeez as my policy testing application, I created a new service in the Security construct of Flow for iPerf as seen below in Figure 15.
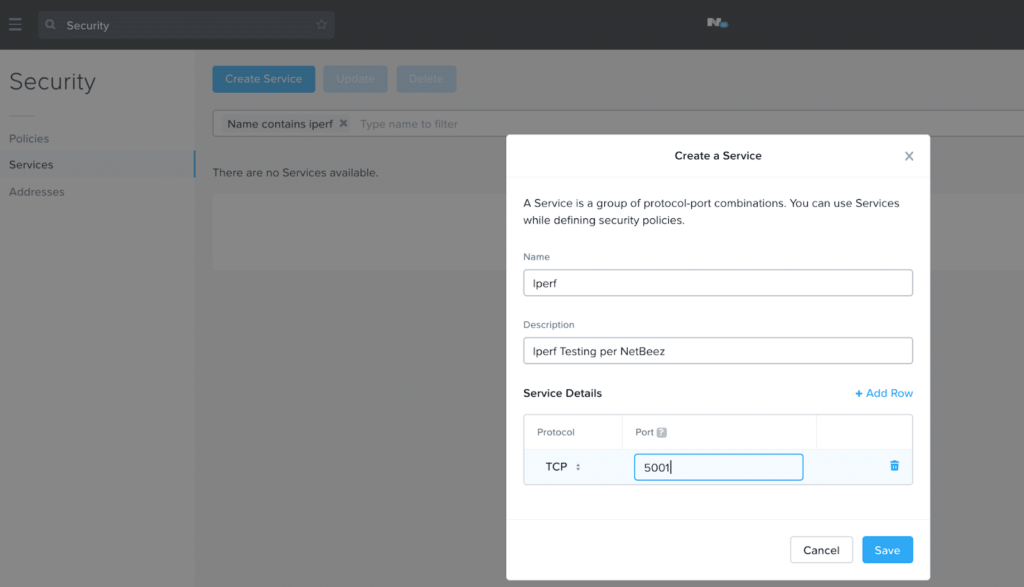
Figure 15
Once this is created, I can add the service to my marketing user in my policy, which will allow my iPerf traffic to test my network bandwidth.
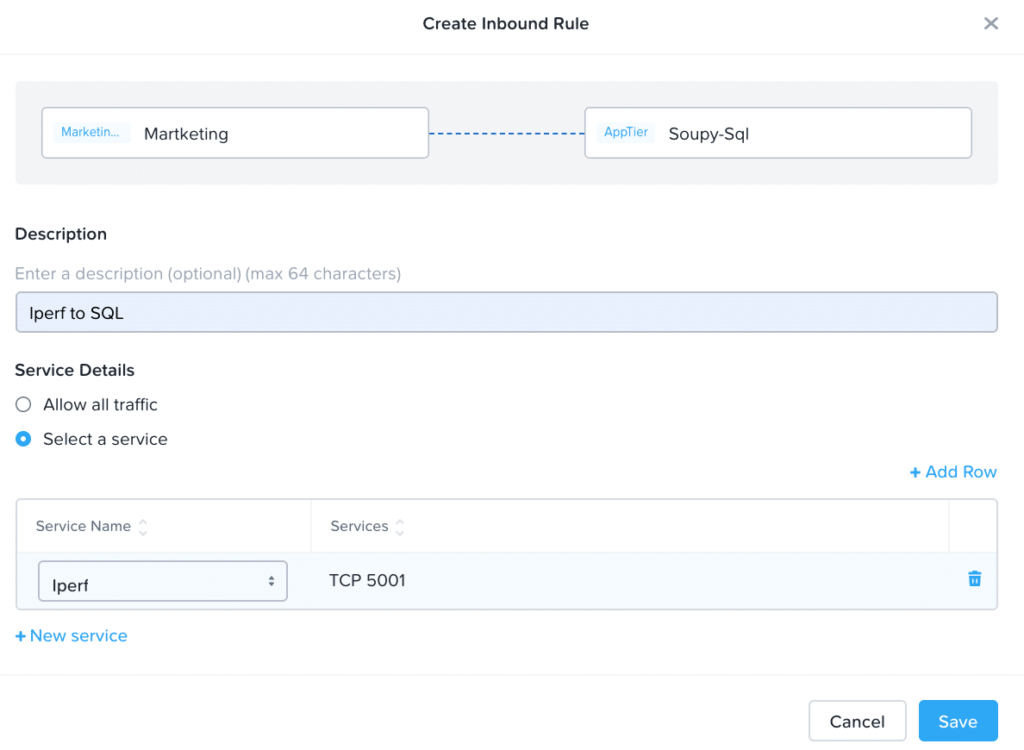
Figure 16
The iPerf Traffic is now allowed from the Marketing Users agent to the SQL Server
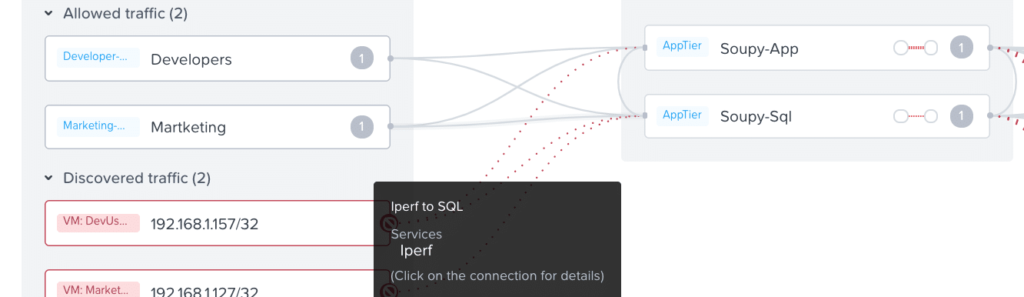
Figure 17
Nutanix Flow Security Central
At Nutanix .Next 2020, Nutanix announced the SaaS Flow Security Central to aid users in enhancing their security posture by giving them visibility into their on-prem Nutanix and cloud resources. With Flow Security Central users see their STIG compliance in platform, security policies in platform, and ensuring your applications in a hybrid cloud deployment. While in its initial deployment the SaaS will provide insights into your applications and show you traffic flows to assist in creating your security posture in a hybrid cloud world.
As you can see in Figure 18, the dashboard will indicate the number of flows within the environment and how many are blocked. You will also get an idea of the number of unprotected VMs in your on-prem infrastructure.
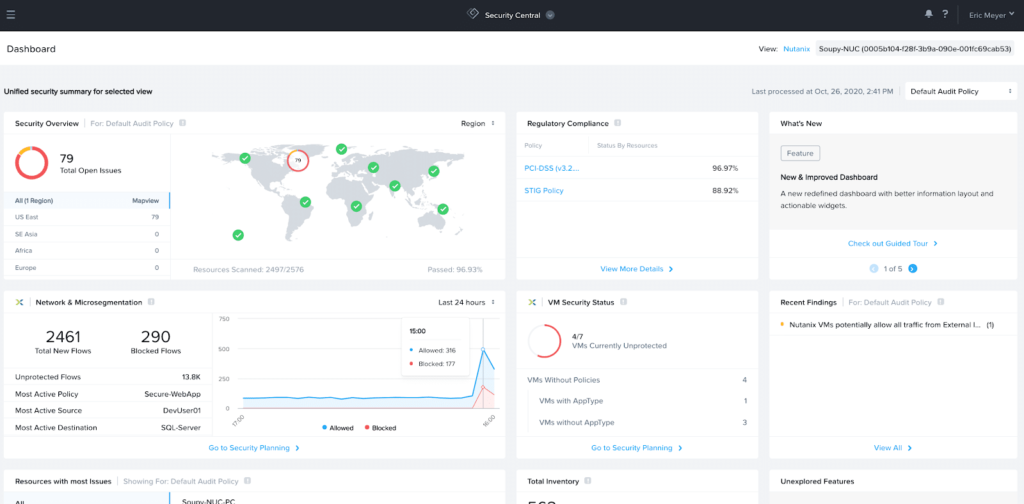
Figure 18
In addition, you can see there are 79 open issues within my environment. Taking a deeper dive into the Regulatory Compliance View, in Figure 19, you can see there are multiple issues in my cluster from a PCI/HIPPA compliance and STIG policies.
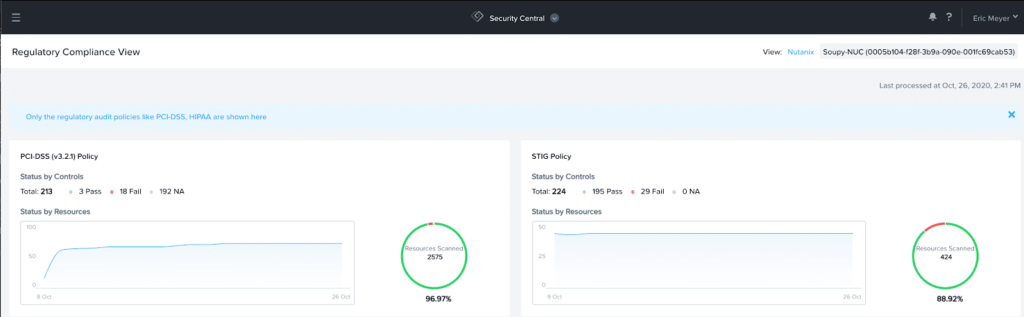
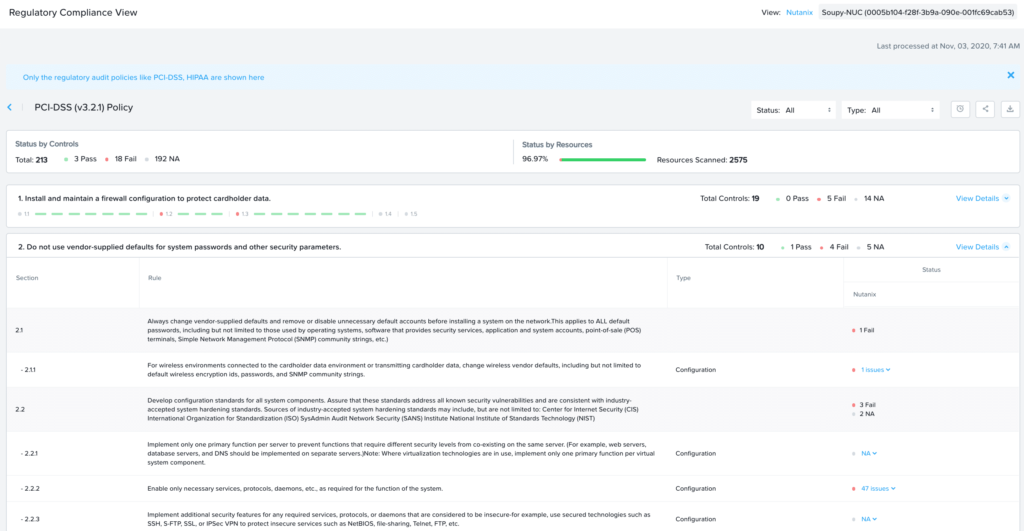
Figure 19
Conclusion
While in this post the NetBeez agents are lightweight Debian VMs, the agent can be installed on a Windows or Linux server in your Nutanix Private Cloud to provide the same network monitoring capability for your critical applications. Thank you to the NetBeez team for spinning up a demo environment for me to test and validate my security policies with a simple to use platform!
About the Author
Eric Meyer is a pre-sales Systems Engineer at Nutanix and has several years of experience in networking, security, and SDN systems. Eric is passionate about delivering and positioning Nutanix Enterprise Cloud solutions within the commercial accounts in the Western Pennsylvania region. He was awarded several certifications from Nutanix, Amazon Web Services, and Nokia.
Find Out More
In addition to the solutions detailed in the BLOG post, end users can use the Nutanix / NetBeez validated solution for network monitoring, performance testing, end user computing monitoring and troubleshooting. To find out more about the Nutanix and NetBeez validated solutions, Nutanix Hybrid Cloud Portfolio, and NetBeez Product details, please visit the following links.
https://www.nutanix.com/products
https://www.nutanix.com/partners/technology-alliances/netbeez
https://netbeez.net/about/partners/
© 2021 Nutanix, Inc. All rights reserved. Nutanix, the Nutanix logo and all Nutanix product, feature and service names mentioned herein are registered trademarks or trademarks of Nutanix, Inc. in the United States and other countries. Other brand names mentioned herein are for identification purposes only and may be the trademarks of their respective holder(s). This post may contain links to external websites that are not part of Nutanix.com. Nutanix does not control these sites and disclaims all responsibility for the content or accuracy of any external site. Our decision to link to an external site should not be considered an endorsement of any content on such a site. This post may contain express and implied forward-looking statements, which are not historical facts and are instead based on our current expectations, estimates and beliefs. The accuracy of such statements involves risks and uncertainties and depends upon future events, including those that may be beyond our control, and actual results may differ materially and adversely from those anticipated or implied by such statements. Any forward-looking statements included herein speak only as of the date hereof and, except as required by law, we assume no obligation to update or otherwise revise any of such forward-looking statements to reflect subsequent events or circumstances.





