In the early days telnet was the standard command to connect to a remote host. The main drawback of telnet is that all communication is sent as clear text, including passwords.
Secure SHell (ssh) came along in 1995 to close the security hole. Since then, it has become the standard for remote host access. In this post, we’ll review how to use ssh without password, while preserving its security.
Password-based ssh
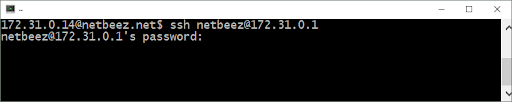
If you use a terminal, the command to connect to a remote host (e.g. 172.31.0.13) is:
ssh user_name@destination
In which case, user_name is the user login name of the account you are connecting to. Destination is the remote host you want to connect to, specified as IP address or Fully Qualified Domain Name (FQDN). You will be prompted to enter a password, and after that, you will connect to the remote Linux host.
Passwords have three main drawbacks:
- Usability: Users have to remember them
- Security: They are insecure against brute force and dictionary attacks
- Automation: If you need to write a script that includes accessing remote hosts, then using password authentication makes the script impractical
Password-less ssh
Password-less ssh is based on public key cryptography. It allows you to connect to a remote host without necessarily having to type in a password. Let’s see how this works:
Create a private-public kay pair
On your CLI type the command ssh-keygen. and hit ENTER. NOTE: For all the following prompts just hit enter. When asked to enter a passphrase, just hit ENTER (we’ll get back to this later). You will see an output as follows:
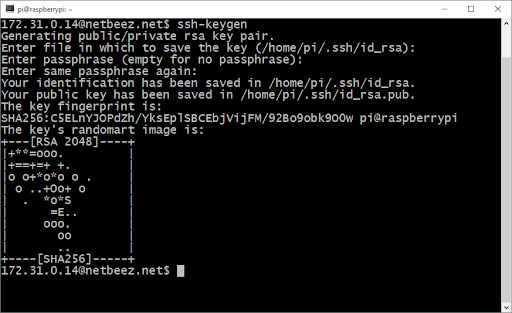
From the output, we can see that it created a private-public key pair saved in /home/pi/.ssh/id_rsa and /home/pi/.ssh/id_rsa.pub respectively. It also tells you that your key length is 2048 bits which is the default value and is considered secure these days. In simple terms, the longer the key the more secure it is against attackers. If you are bit more paranoid, you can use 4096-big long key by using “ssh-keygen -b 4096.” If you try this you will notice that it takes much longer to generate the key pair–security comes at a cost.
From those two files, the private key (/home/pi/.ssh/id_rsa) is the one you need to save and keep private. The public key can be freely distributed to anyone without compromising security.
Copy the public key to the remote host
In order to connect to a remote host with your private key, first copy the public key on it. This needs to be done only once. You can use the following command:
ssh-copy-id user_name@destination
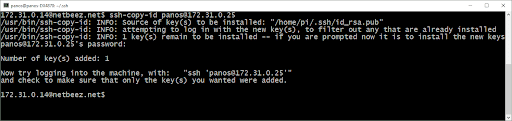
The output informs you that it has copied your public key to the destination. What this does on the backend is to append your public key in the file /home/user_name/.ssh/authorized_keys. The destination host uses that authorized_keys file to determine which private keys are trusted. If you don’t have ssh-copy-id you can use the following command:
cat .ssh/id_rsa.pub | ssh user_name@destination ‘cat >> .ssh/authorized_keys’
Connecting via ssh without password
Now, the next time you try to connect to the destination host, you only have to type ‘ssh user_name@destination’ and you will be welcomed without any password. The first time I used this, it felt like magic! Of course, you need to copy your public key to each host you need to connect to.
Similar to using a password, the security of passwordless ssh is contingent upon on keeping your private key private. It is much more difficult to break key-pair encryption with brute force attack than using a password.
For the more paranoid ones…
Now if you want to add another level of security to your private key, you can enter a passphrase when prompted by the command ‘ssh-keygen’ The passphrase is like a password (I am not sure why they call it a passphrase and not a password), and it’s tight to your private key. You can remove it or change it in the future if need be. Keep in mind that each time you ssh with your private key, you will have to enter the passphrase.
A practical use of the private-public key encryption is when you need to give or get temporary access to a remote Linux host. Let’s say a friend is asking for help to troubleshoot something on his Linux box. If he wants to give you access to it, you can send him your public key (/home/pi/.ssh/id_rsa.pub–remember you can freely share this without compromising security), he can append it in his /home/user_name/.ssh/authorized_keys, and then you can ssh to the machine with ssh user_name@destination. When you are done, he can just remove your public key from his /home/user_name/.ssh/authorized_keys. Compare that to giving you the password of a local account, and then having to change the password or delete the account.
Another important benefit of password-less ssh is the ability to write scripts that run independently and can get access to remote hosts to perform various tasks. We’ll give examples of those in a future post. I hope that you enjoyed learning about ssh, stay tuned for the next Linux for Network Engineers blog post!