Open networks are highly insecure and can lead to eavesdropping on communications. Additionally, there’s no mutual authentication in an open network to depict which access point a client is connecting to. How does one know if the access point that is accepting connections is actually trustworthy and not a rogue access point?
Secure communications between a client and access point require authentication and encryption. An access point broadcasting a secure SSID will advertise its security capabilities in the Robust Security Network Association (RSNA) Information Element.
The RSNA is used in either a pre-shared key (PSK) or 802.1X SSID, in other words, WPA2-Personal or WPA2-Enterprise.
The 4-Way Handshake utilizes an exchange of four EAPOL-Key frames between the client and access point. In a PSK network, the exchange of frames occurs after the Open System Authentication and Association. In an 802.1X network, the 4-Way Handshake occurs after EAP authentication.
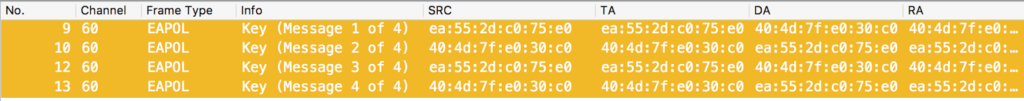
From the image above, there are four messages exchanged between the client and access point. Each message has a specific purpose:
The client and access point will derive their own separate pairwise transient key (PTK). The PTK is derived from each device’s pairwise master key (PMK). The PTK is comprised of the access point’s ANonce, client’s SNonce, and the MAC addresses of the access point and client.
To follow the frame exchanges, the graphic is presented below:
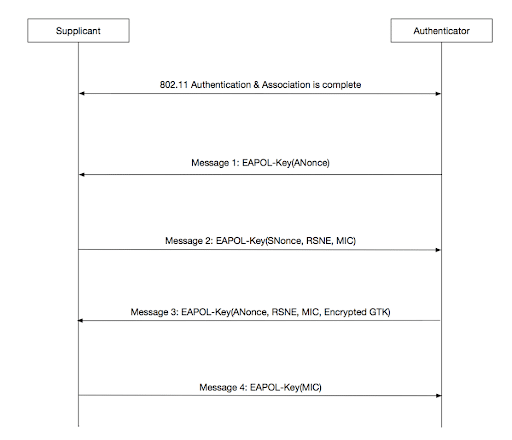
In message 1, the access point sends an EAPOL-Key frame to the client, containing the its ANonce which will be used to generate a PTK. This frame also contains other fields in the information element describing the type of encryption that is being used, such as AES cipher.
In message 2, the client sends its EAPOL-Key frame to the access point. This frame contains the SNonce, RSN Element, and the MIC (Message Integrity Code), allowing the client to derive a PTK from the SNonce and ANonce.
Message 3 (which is sent by the access point) contains an ANonce, RSN Element, and a MIC. What’s important about message 3 is the transportation of the Group Temporal Key (GTK) which is used to protect broadcast and multicast frames.
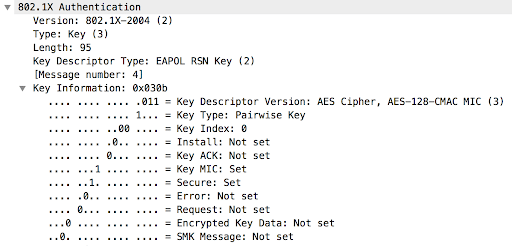
Message 4 is sent by the client which and contains a MIC. It is the final frame from the 4-Way Handshake. This final message notifies the access point of whether the temporal keys were installed successfully or not. This can be identified by the subfields of Key MIC: Set and Secure: Set.
Vulnerabilities of the 4-Way Handshake
In 2018, it was announced there was a vulnerability within the 4-Way Handshake. The “KRACK Attack” proved to be able to target the weaknesses in the key re-installation process. Shortly after, another technique was identified through the use of a single EAPOL-Key frame.
The future of the 4-Way Handshake lies within WPA3 – the change involves the use of Simultaneous Authentication of Equals (SAE). Instead, a fresh PMK is negotiated in an SAE handshake. Following the 4-Way Handshake will be the formation of the fresh PMK with the SAE process. The result is protected against the previous two vulnerabilities that I had described above.
About the Author:
Rowell Dionicio is a network engineer for a west coast university specializing in Wi-Fi design, deployment, and troubleshooting. He supports a WLAN infrastructure with over 40k concurrent Wi-Fi devices in higher education. He is the co-host of the Wi-Fi focused ClearToSend podcast, and is co-host on a YouTube show ‘WiFi of Everything’. You can engage with him on Twitter @rowelldionicio where he encourages open communication.





