A few weeks ago, we released a new feature in NetBeez called Custom Command, which we introduced in our previous blog post. Custom Command enable users to create their own monitoring scripts and run them directly from NetBeez agents, giving even more flexibility in adapting the platform to your unique operational needs.
Why Detect Rogue SSIDs?
In enterprise environments, consistent and well-managed SSIDs ensure seamless connectivity, enforce security policies, and provide the foundation for network segmentation.
Rogue SSIDs can pose significant security risks. These unauthorized networks can lure employees into connecting, potentially exposing sensitive company data or providing an attack vector for malicious actors. By actively scanning and identifying rogue SSIDs, IT teams can strengthen wireless security and maintain a trusted Wi-Fi environment.
Custom Script to Detect Rogue SSIDs
With NetBeez Custom Command, you can easily implement a script that scans for nearby SSIDs, compares them against an approved list, and alerts if rogue SSIDs are detected.
Using an LLMs these days would be the recommended first step to implement a script to accomplish this goal. With a few iterations you should be able to develop the script.
Here is the first prompt I provided to ChatGPT:
I want a bash script to detect rogue SSIDs. The script should have an array at the beginning where you declare the approved SSIDs. Then it should do a scan with sudo iw and it should compare the array with the SSIDs from the scan and have a counter that shows how many rogue SSIDs have been detected. Then it should print the output in the format: echo “rogue_ssids=${rogue_ssids}”
From this starting point, the script was enhanced to not only count rogue SSIDs but also display their names in a clear format:
ERROR: <number_of_rogue_SSIDs>: ssid1 ssid2 ssid3
rogue_ssids=<count>This makes it straightforward to integrate with NetBeez alerts and dashboards.
The final script is as follows:
#!/usr/bin/env bash
# Approved SSIDs (modify this list)
approved_ssids=("netbeez" "netbeez-ipv6" "netbeez-ubi")
# Interface to scan on (change if needed)
iface="wlan0"
# Scan for SSIDs (unique list)
scanned_ssids=$(sudo iw dev "$iface" scan 2>/dev/null | grep -oP '(?<=SSID: ).*' | sort -u)
rogue_list=()
# Compare scanned SSIDs with approved list
while IFS= read -r ssid; do
if [[ -n "$ssid" && ! " ${approved_ssids[*]} " =~ " ${ssid} " ]]; then
rogue_list+=("$ssid")
fi
done <<< "$scanned_ssids"
# Count rogue SSIDs
rogue_count=${#rogue_list[@]}
# Print error line if rogues found
if [[ $rogue_count -gt 0 ]]; then
echo "ERROR: Rogue SSIDs count:${rogue_count}: Rogue SSIDs List: ${rogue_list[*]}"
fi
# Always print final rogue count
echo "rogue_ssids=${rogue_count}"
Rogue SSID Implementation
On the NetBeez Dashboard I created a new Custom Command and pasted the detection script. The script will run every hour on the hour:
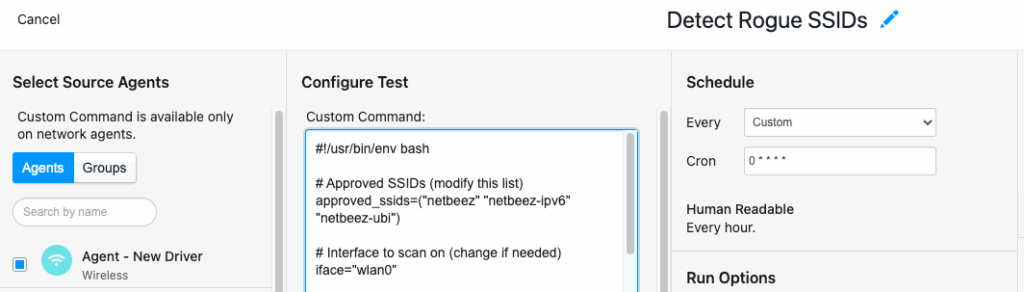
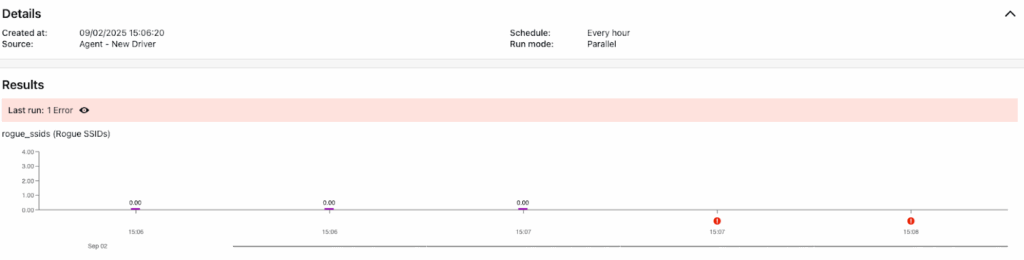
The script initially didn’t detect any rogue SSIDs, so it’s output was showing 0 count. Once a rogue SSID is detected it shows up as an error on the dashboard as follows:
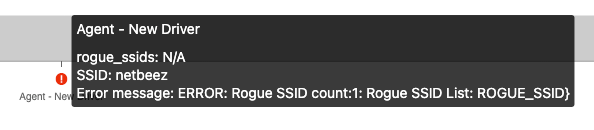
The details of the alert show the rogue SSID name: “ROGUE_SSID”
Conclusions
The ability to detect rogue SSIDs is a critical part of securing enterprise Wi-Fi environments. Unauthorized access points can easily compromise sensitive data and reduce employee trust in the network. NetBeez’s Custom Command provide IT teams with a lightweight but powerful solution to proactively identify these risks. By running detection scripts directly from agents and visualizing the results in the NetBeez dashboard, administrators gain immediate insight and actionable alerts. This combination of automation and visibility strengthens network security while reducing manual overhead.





